
Let us apply ACL (Access Control List) on the topology. First, let us assign IP addresses and change the state of the interfaces.

Here, the status is change as shown in the following diagram.

Then, we will have to assign IP addresses to the PCs.

And the PC attach to the other interface. Please note the difference between default gateways. We assign fast Ethernet interface address to default gateway.

Thus, after applying IP addresses. We see that Packet transfer is successful.

Let us apply ACL and permit and deny Hosts IP’s as we want. We are going to deny and permit certain hosts as follows.

Let us apply ACL and permit and deny Hosts IP’s as we want.
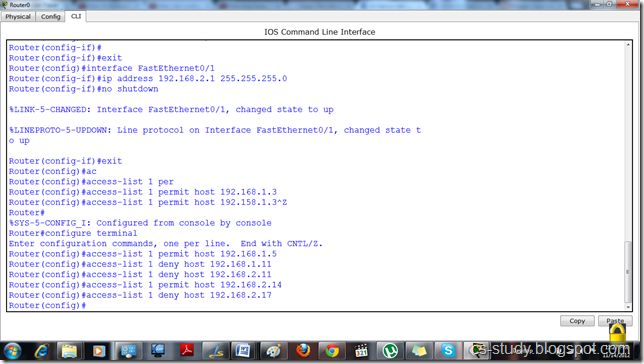
Then, we will have to tell the interface that which ACL to follow. ACL is uniquely identified with the number, in this case 1.

Now, you see that the denied will not be able to send the data while those who we permit can send packet.

Similarly, in the bottom right corner you can see status.




thank you so much.. it was really useful to me!!
ReplyDeleteYou are Welcome :)
Deletehow to delete access list
ReplyDeleteno access-list "#"
Deletejust enter the delete command
DeleteThnx
ReplyDeletenot working!
ReplyDeletejoke!hahaha
were can i find a complete bbok just for acl configuration
ReplyDeletehow i can block access a network to other network but the other network can access the blocked network
ReplyDeletethis is cool site..i love it...easy way to understand..
ReplyDeleteReally use full this type
ReplyDeleteFile tracking and auditing
ReplyDeleteSecure File sharing - Add file access control and file IOs monitor on the fly with Windows file system mini-filter driver component in C#, C++ demo source code.
ReplyDeleteNice information.. Thanks for sharing. DACCESS provides you designed and developed access control system on open flexible technology to provide real-time monitoring, management and control of your access system.
access control system
How to delete accesslist
ReplyDelete