Network Security and Virtual Private Networks
Objective
The objective of this lab is to study the role of firewalls and Virtual Private Networks (VPNs) in providing security to shared public networks such as the Internet.
Overview
Computer networks are typically a shared resource used by many applications for many different purposes. Sometimes the data transmitted between application processes is confidential, and the application users would prefer that others not be able to read it.
A firewall is a specially programmed router that sits between a site and the rest of the network. It is a router in the sense that it is connected to two or more physical networks and it forwards packets from one network to another, but it also filters the packets that flow through it. A firewall allows the system administrator to implement a security policy in one centralized place. Filter-based firewalls are the simplest and most widely deployed type of firewall. They are configured with a table of addresses that characterize the packets they will and will not forward.
A VPN is an example of providing a controlled connectivity over a public network such as the Internet. VPNs utilize a concept called an IP tunnel—a virtual point-to-point link between a pair of nodes that are actually separated by an arbitrary number of networks. The virtual link is created within the router at the entrance to the tunnel by providing it with the IP address of the router at the far end of the tunnel. Whenever the router at the entrance of the tunnel wants to send a packet over this virtual link, it encapsulates the packet inside an IP datagram. The destination address in the IP header is the address of the router at the far end of the tunnel, while the source address is that of the encapsulating router.
In this lab you will set up a network where servers are accessed over the Internet by customers who have different privileges. You will study how firewalls and VPNs can provide security to the information in the servers while maintaining access for customers with the appropriate privilege.
Procedure
Create a New Project
1. Start OPNET IT Guru Academic Edition ⇒ Choose New from the File menu.
2. Select Project and click OK ⇒ Name the project <your initials>_VPN, and the scenario NoFirewall ⇒ Click OK.
3. Click Quit on the Startup Wizard.
4. To remove the world background map, select the View menu ⇒ Background ⇒ Set Border Map ⇒ Select NONE from the drop-down menu ⇒ Click OK.
Create and Configure the Network
The ppp_server and ppp_wkstn support one underlying SLIP (Serial Line Internet Protocol) connection at a selectable data rate.
PPP DS1 connects two nodes running IP. Its data rate is 1.544 Mbps.
Initialize the Network:
1. Open the Object Palette dialog box by clicking  . Make sure that the internet_toolbox item is selected from the pull-down menu on the object palette.
. Make sure that the internet_toolbox item is selected from the pull-down menu on the object palette.
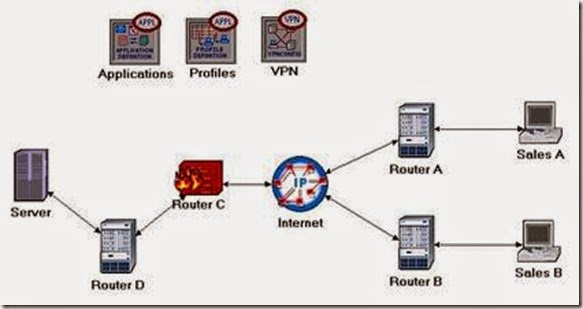
2. Add the following objects, from the palette, to the project workspace (see figure below for placement): Application Config, Profile Config, an ip32_cloud, one ppp_server, three ethernet4_slip8_gtwy routers, and two ppp_wkstn hosts.
a. To add an object from a palette, click its icon in the object palette ⇒ Move your mouse to the workspace and click where you want to place the object ⇒ Right-click to indicate you are done creating objects of this type.
- Rename the objects you added and connect them using PPP DS1 links, as shown below:
4. Save your project.
Several example application configurations are available under the Default setting. For example, "Web Browsing (Heavy HTTP1.1)" indicates a Web browsing application performing heavy browsing using HTTP 1.1 protocol..
Configure the Nodes:
- Right-click on the Applications node ⇒ Edit Attributes ⇒ Assign Default to the Application Definitions attribute ⇒ Click OK.
- Right-click on the Profiles node ⇒ Edit Attributes ⇒ Assign Sample Profiles to the Profile Configuration attribute ⇒ Click OK.
- Right-click on the Server node ⇒ Edit Attributes ⇒ Assign All to the
Application: Supported Services attribute ⇒ Click OK.
4. Right-click on the Sales A node ⇒ Select Similar Nodes (make sure that both Sales A and Sales B are selected).
i. Right-click on the Sales A node ⇒ Edit Attributes ⇒ Check the Apply Changes to Selected Objects check-box.
ii. Expand the Application: Supported Profiles attribute ⇒ Set rows to 1 ⇒ Expand the row 0 hierarchy ⇒ Profile Name = Sales Person (this is one of the “sample profiles” we configured in the Profiles node).
iii. Click OK.
5. Save your project.
Choose the Statistics
DQ Query Response Time is measured from the time when the database query application
sends a request to the server to the time it receives a response packet.
HTTP Page Response Time specifies the time required to retrieve the entire page with all the contained inline objects.
1. Right-click anywhere in the project workspace and select Choose Individual Statistics from the pop-up menu.
2. In the Choose Results dialog, check the following statistics:
i. Global Statistics ⇒ DB Query ⇒ Response Time (sec).
ii. Global Statistics ⇒ HTTP ⇒ Page Response Time (seconds).
3. Click OK.
4. Right-click on the Sales A node and select Choose Individual Statistics from the pop-up menu.
5. In the Choose Results dialog, check the following statistics:
i. Client DB ⇒ Traffic Received (bytes/sec).
ii. Client Http ⇒ Traffic Received (bytes/sec).
6. Click OK.
7. Right-click on the Sales B node and select Choose Individual Statistics from the pop-up menu.
8. In the Choose Results dialog, check the following statistics:
i. Client DB ⇒ Traffic Received (bytes/sec).
ii. Client Http ⇒ Traffic Received (bytes/sec).
9. Click OK and then save your project.
The Firewall Scenario
In the network we just created, the Sales Person profile allows both sales sites to access applications such as Database Access, Email, and Web Browsing from the server (check the Profile Configuration of the Profiles node). Assume that we need to protect the database in the server from external access, including the salespeople. One way to do that is to replace Router C with a firewall as follows:
1. Select Duplicate Scenario from the Scenarios menu and name it Firewall ⇒
Click OK.
2. In the new scenario, right-click on Router C ⇒ Edit Attributes.
3. Assign ethernet2_slip8_firewall to the model attribute.
4. Expand the hierarchy of the Proxy Server Information attribute ⇒ Expand the row 1, which is for the Database application, hierarchy ⇒ Assign No to the Proxy Server Deployed attribute as shown:
Proxy Server Information is a table defining the configuration of the proxy servers on the firewall. Each row indicates whether a proxy server exists for a certain application and the amount of additional delay that will be introduced to each forwarded packet of that application by the proxy server.
5. Click OK and then save your project.
Our Firewall configuration does not allow database-related traffic to pass through the firewall (it filters such packets out). This way, the databases in the server are protected from external access. Your Firewall scenario should look like the following figure.
The Firewall_VPN Scenario
In the Firewall scenario, we protected the databases in the server from “any” external access using a firewall router. Assume that we want to allow the people in the Sales A site to have access to the databases in the server. Since the firewall filters all database-related traffic regardless of the source of the traffic, we need to consider the VPN solution. A virtual tunnel can be used by Sales A to send database requests to the server. The firewall will not filter the traffic created by Sales A because the IP packets in the tunnel will be encapsulated inside an IP datagram.
1. While you are in the Firewall scenario, select Duplicate Scenario from the Scenarios menu and give it the name Firewall_VPN ⇒ Click OK.
2. Remove the link between Router C and the Server.
3. Open the Object Palette dialog box by clicking  . Make sure that the opened palette is the one called internet_toolbox.
. Make sure that the opened palette is the one called internet_toolbox.
i. Add to the project workspace one ethernet4_slip8_gtwy and one IP VPN Config (see the figure below for placement).
ii. From the Object Palette, use two PPP DS1 links to connect the new router to Router C (the firewall) and to the Server, as shown below.
iii. Close the Object Palette dialog box.
4. Rename the IP VPN Config object to VPN.
5. Rename the new router to Router D as shown:
Configure the VPN:
- Right-click on the VPN node ⇒ Edit Attributes.
i. Expand the VPN Configuration hierarchy ⇒ Set rows to 1 ⇒ Expand row 0 hierarchy ⇒ Edit the value of Tunnel Source Name and write down Router A ⇒ Edit the value of Tunnel Destination Name and write down Router D.
ii. Expand the Remote Client List hierarchy ⇒ Set rows to 1 ⇒ Expand row 0 hierarchy ⇒ Edit the value of Client Node Name and write down Sales A.
iii. Click OK and then save your project.
Run the Simulation
To run the simulation for the three scenarios simultaneously:
1. Go to the Scenarios menu ⇒ Select Manage Scenarios.
2. Change the values under the Results column to <collect> (or <recollect>) for the three scenarios. Keep the default value of the Sim Duration (1 hour). Compare to the following figure.
3. Click OK to run the three simulations. Depending on the speed of your processor, this may take several minutes to complete.
4. After the three simulation runs complete, one for each scenario, click Close ⇒ Save your project.
View the Results
To view and analyze the results:
1. Select Compare Results from the Results menu.
2. Expand the Sales A hierarchy ⇒ Expand the Client DB hierarchy ⇒ Select the
Traffic Received statistic.
3. Change the drop-down menu in the middle-lower part of the Compare Results dialog box from As Is to time_average as shown.
5. Create a graph similar to the previous one, but for Sales B:
- Create two graphs similar to the previous ones to depict the Traffic Received by the Client Http for Sales A and Sales B.
Note: Results may vary slightly due to different node placement.












Platinum FREE Download Business Voip Solutions with DU solution.I like the helpful information you provide in your articles. I will bookmark your blog and check again here regularly.
ReplyDelete
ReplyDeleteनोटबंदी के 50वें दिन, मोदी सरकार के फैसले से निराश हैं जनता
Readmore todaynews18.com https://goo.gl/NJUQY9
This comment has been removed by the author.
ReplyDeletelearn to improve your study time - www.getthefactsabout.com/alpha-levo-energize-brain-booster-review
ReplyDeleteFree Internet Learning Join people learning internet together at computergk. Enjoy free online internet learning courses from top universities and specialist organisations. Start learning now.
ReplyDeleteWow, cool post. I'd like to write like this too - taking time and real hard work to make a great article... but I put things off too much and never seem to get started. Thanks though. torrenting without vpn
ReplyDeleteI really like your writing style, great information, thankyou for posting. anime torrents
ReplyDeleteI appreciate everything you have added to my knowledge base.Admiring the time and effort you put into your blog and detailed information you offer.Thanks. setup vpn iphone
ReplyDeleteThis post is very unique and informative for all. Impressive information you share in this. Keep it up and keep sharing.
ReplyDeleteartificial intelligence internship | best final year projects for cse | internship certificate online | internship for mba finance students | internship meaning in tamil