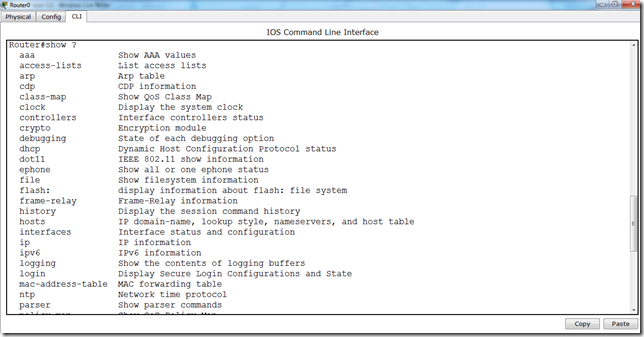
There are various common commands that one needs to be familiar with. These commands will be used all the time.
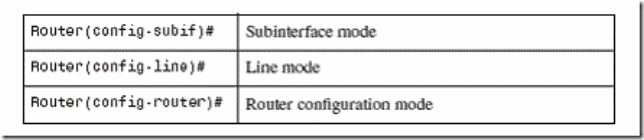
There are different modes. All modes have their own distinct commands.
All the configuration commands will be written in configuration mode.
Using the tab Key to Complete Commands
When you are entering a command, you can use the tab key to complete the command. Enter the first few characters of a command and press the tab key. If the characters are unique to the command, the rest of the command is entered in for you. This is helpful if you are unsure about the spelling of a command. For example, if we write in enable mode, “sh” and press tab button, “show” command will be written on the CLI mode.
Router Modes
TIP: There are other modes than these. Not all commands work in all modes. Be
careful. If you type in a command that you know is correct—show running-config, for example—and you get an error, make sure that you are in the correct mode.
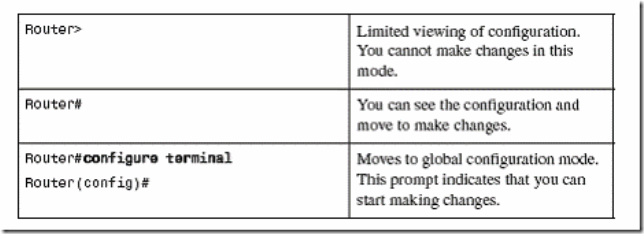
Entering Global Configuration Mode
Configuring a Router Name
This command works on both routers and switches.
Configuring Passwords
These commands work on both routers and switches.
Here it is important to know that the enable secret password is encrypted by default. The enable password is not. For this reason, recommended practice is that you never use the enable password command. Use only the enable secret password command in a router or switch configuration. You cannot set both enable secret password and enable password to the same password. By doing so, it defeats the use of encryption.
Show Commands:
There are various show commands. in order to get familiar with these commands just write “show ?” in the enable mode.
Similarly, there are various commands that shows us the configurations that we have done on our router or any other device depending on the device we are working on. We will talk about later on.
Similarly, there are various commands in the configuration mode which we attain by entering the following command
Router# configure terminal.
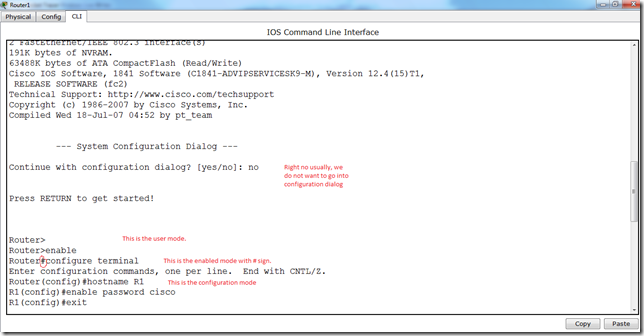
Look at the following diagram.
Ok, so now lot of things are happening here. Red markers explain them, also we are setting the hostname of the router and we have successfully applied the password by the following command.
enable password cisco
Here, “cisco” is the password.
Similarly, the command
router#show ip interface brief
gives us the information about the interfaces of the router. Now, detail discussion on the interfaces will be done later.

![clip_image002[6] clip_image002[6]](http://lh3.ggpht.com/--dpKj3r9sEU/UH79S5UpYXI/AAAAAAAAATw/jirihOhY43k/clip_image002%25255B6%25255D_thumb%25255B11%25255D.gif?imgmax=800)
![clip_image002[16] clip_image002[16]](http://lh4.ggpht.com/-1GGW7JYR68A/UH8CcHOICII/AAAAAAAAAUU/9FfwQV8iQ50/clip_image002%25255B16%25255D_thumb%25255B5%25255D.gif?imgmax=800)
![clip_image002[18] clip_image002[18]](http://lh3.ggpht.com/-2i-FgOiwxNU/UH8ClpARinI/AAAAAAAAAVE/6icaKbK1O5c/clip_image002%25255B18%25255D_thumb%25255B1%25255D.gif?imgmax=800)
![clip_image004[5] clip_image004[5]](http://lh3.ggpht.com/-F1TMwYxKpNU/UH8CorINLdI/AAAAAAAAAVU/Qyiz-ODsitM/clip_image004%25255B5%25255D_thumb%25255B1%25255D.gif?imgmax=800)